ISC2 CISSP Boot Camp
Award-winning Official ISC2 CISSP exam preparation for the rigorous CISSP adaptive exam.
Hello, you are using an old browser that's unsafe and no longer supported. Please consider updating your browser to a newer version, or downloading a modern browser.
4 Days
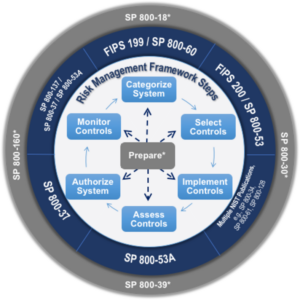
Our Risk Management Framework (RMF) V2.0 for Federal Agencies course is a 4-day comprehensive deep dive into the Risk Management Framework prescribed by NIST Standards.
During this course, you will participate in scenario-based exercises to enhance understanding of the processes used for system authorization, including all of the elements of the Risk Management Framework. It is designed for federal employees and contractors in non-DoD agencies, and for any supporting vendors and service providers.

RMF overview
Key concepts including assurance, assessment, authorization
Security controls
Security laws, policy, and regulations
System Development Life Cycle (SLDC)
Documents for cyber security guidance
Tasks and responsibilities for RMF roles
Overview of risk management
Four-step risk management process
Tasks breakdown
Risk assessment reporting and options
Step key references and overview
Sample SSP
Task 1-1: Security Categorization
Task 1-2: Information System Description
Task 1-3: Information System Registration
Lab: The Security Awareness Agency
Step key references and overview
Task 2-1: Common Control Identification
Task 2-2: Select Security Controls
Task 2-3: Monitoring Strategy
Task 2-4: Security Plan Approval
Lab: Select Security Controls
Step key references and overview
Task 3-1: Security Control Implementation
Task 3.2: Security Control Documentation
Lab: Security Control Implementation
Step key references and overview
Task 4-1: Assessment Preparation
Task 4-2: Security Control Assessment
Task 4-3: Security Assessment Report
Task 4-4: Remediation Actions
Task 4-5: Final Assessment Report
Lab: Assessment Preparation
Step key references and overview
Task 5-1: Plan of Action and Milestones
Task 5-2: Security Authorization Package
Task 5-3: Risk Determination
Task 5-4: Risk Acceptance
Lab Step 5: Authorizing Information Systems
Step key references and overview
Task 6-1: Information System & Environment Changes
Task 6-2: Ongoing Security Control Assessments
Task 6-3: Ongoing Remediation Actions
Task 6-4: Key Updates
Task 6-5: Security Status Reporting
Task 6-6: Ongoing Risk Determination & Acceptance
Task 6-7: Information System Removal & Decommissioning
Continuous Monitoring
Security Automation Domains
Lab: Info System & Environment Changes
Answers to Review Questions
Lab Exercise Answers
Get skilled, get certified. We offer a wide range of solutions trusted by thousands of organizations. Fill out a contact form and one of our Enterprise Solutions experts will contact you to discuss the best training solutions for your team. You can also e-mail our team directly at: es-helpdesk@52.47.190.187
Get Pricing & Schedule